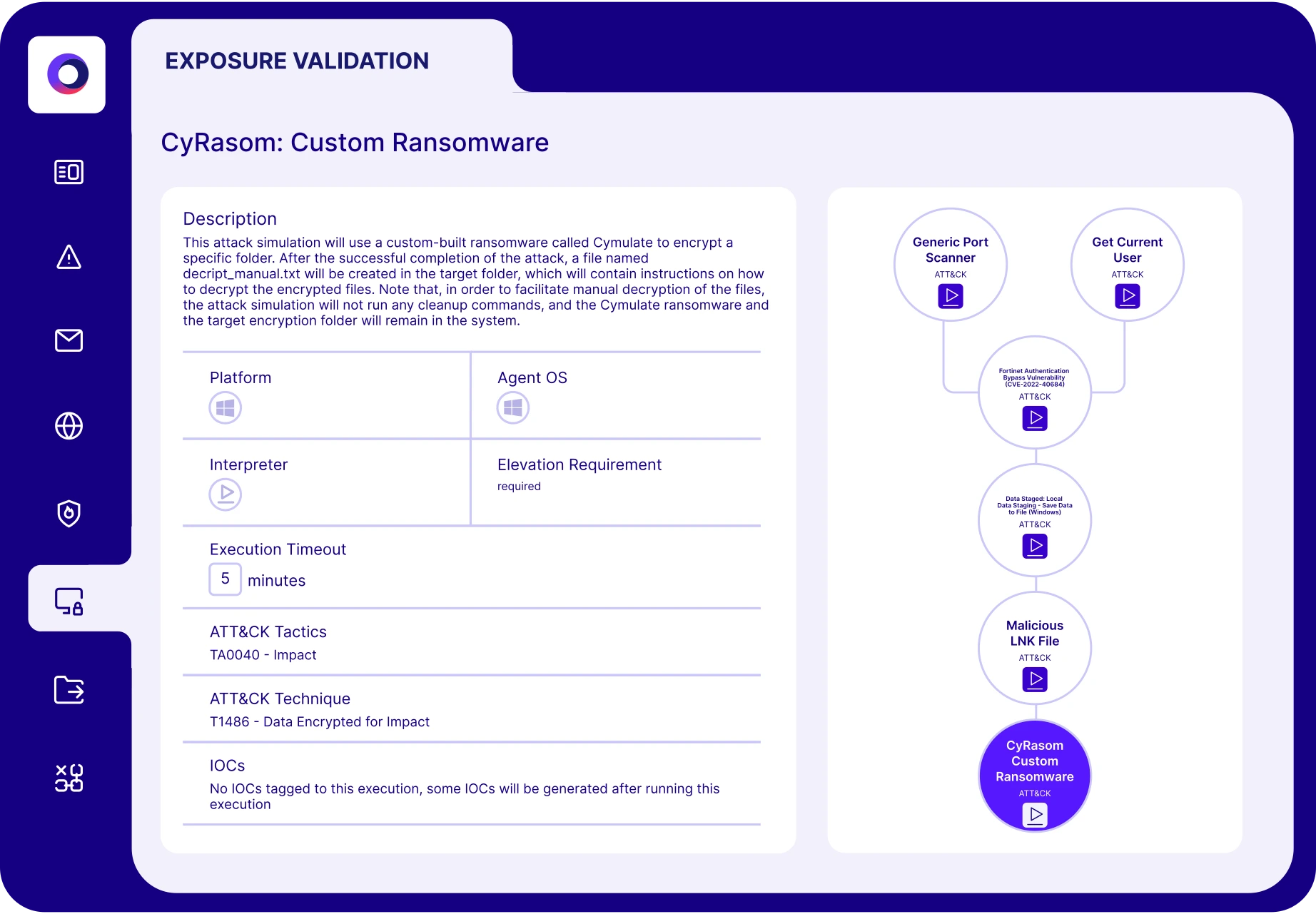
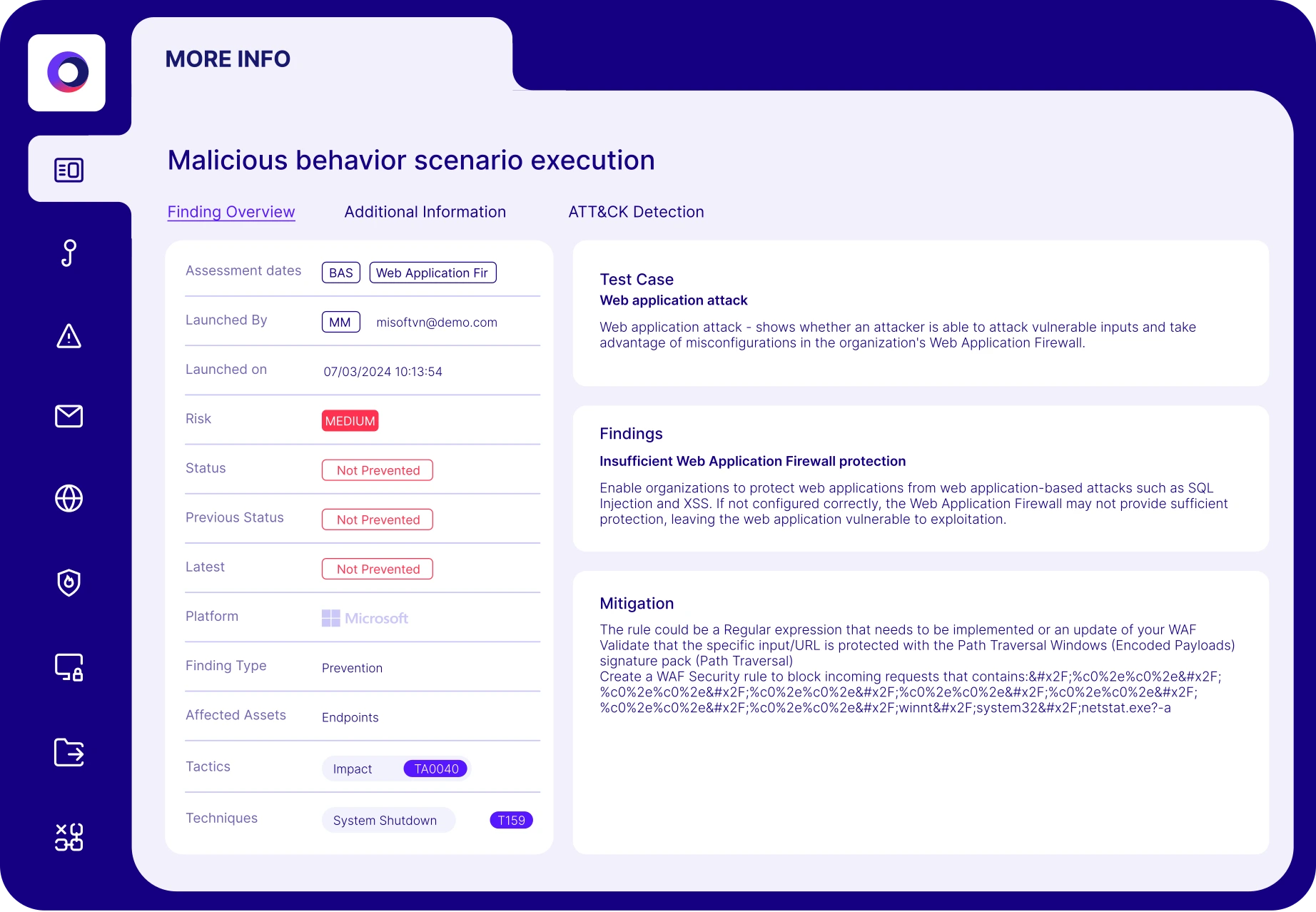
Cymulate for Red Teams
Automate security validation to map attack paths and execute custom attack chains, scaling offensive testing for advanced threats.
A well-structured red team exercise typically takes more than 2 months:
24-72 Hours
Gather, process, validate new threat intelligence
1-2 Weeks
Create custom attack scenarios from intel
1-4 Weeks
Run a red team exercise with realistic testing
2-6 Weeks
Map findings to MITRE and suggest mitigations
Exposure Validation Built for Red Teams
Cymulate Exposure Validation automates and scales red teaming with threat-informed security assessments, allowing you to fast-track your red teaming exercises to identify the most critical security gaps and deliver actionable results.
Solution Results
60%
Increase in red team efficiency
Finance Company
70%
Fewer vulnerabilities in next pen test
IT Organization
3X
Faster at assessing emerging threats
Financial Services
Solution Benefits
What our customers say about us
Organizations across all industries choose Cymulate for automating and scaling red teaming with production-safe security assessments.
GET A PERSONALIZED DEMO
Want to test more frequently with more customization?
“Cymulate allows us to extensively scale our red team activities with only one red teamer.”
– Assistant Information Security Manager, Financial Services Company
Red Teaming FAQs
Cymulate Exposure Validation automates and scales red teaming with production-safe security assessments that include custom attack chains, attack path discovery and MITRE ATT&CK coverage backed by a library of more than 100,000 attack actions. Cymulate findings encourage collaboration between red and purple teams because they include MITRE ATT&CK mappings, remediation guidance, recommended IoCs and custom detection rules that can be directly applied to controls.
Cymulate Exposure Validation can execute simulated assessments at scale from a library of 100,000+ assessments mapped across the full MITRE ATT&CK framework. The attack scenario library is updated daily based on new threat intelligence, so red teamers can focus on building custom attacks and spend less time investigating new threats.
Yes. The Attack Scenario Workbench lets you create custom chains with simple no-code workflows and allows you to upload your own threat scenarios.
Yes. Cymulate assessments focus on security control behavior to lower the risk of blue screens or production disruption.
You can use the MITRE ATT&CK heatmap to visualize emulation coverage and quickly see techniques or sub-techniques that need immediate attention.
Yes. Cymulate Attack Path Discovery allows you to simulate an attacker who has compromised a single workstation and is moving laterally in search of additional assets. The process uncovers lateral movement gaps, privilege escalation paths and exposed data or credentials that attackers can exploit.